This is obvious for all of us working with Citrix technologies that StoreFront (and Web Interface before) is the central place where all company resources like applications and desktops available for any particular user are aggregated and displayed to make access to these resources easy and intuitive. There are many posts with short or long description of installation process – you can find such post also on my blog 🙂 but it’s no so easy to find the answer to the questions: where in our infrastructure StoreFront server should be located and what are the main criteria to select proper location for this service.
The location in which you deploy the StoreFront depends on a number of factors, including:
- Security – verify required security level and select the scenario which will be complaint with approved company standards.
- Authentication – when users log on, either NetScaler Gateway or the StoreFront can authenticate user credentials. The location where you place the StoreFront in your network is a factor that determines, where users will be authenticated.
- User software – users can connect to the StoreFront with either the NetScaler Gateway Plug-in or Citrix Receiver. You can limit the resources users can access by using Citrix Receiver only, or give users greater network access with the NetScaler Gateway Plug-in. How users connect, and the resources to which you allow users to connect can help determine where you deploy the StoreFront in your network.
The configuration of your network and your security policies determines where you deploy StoreFront to allow remote users to access published resources. Three possible StoreFront deployment scenarios are the following:
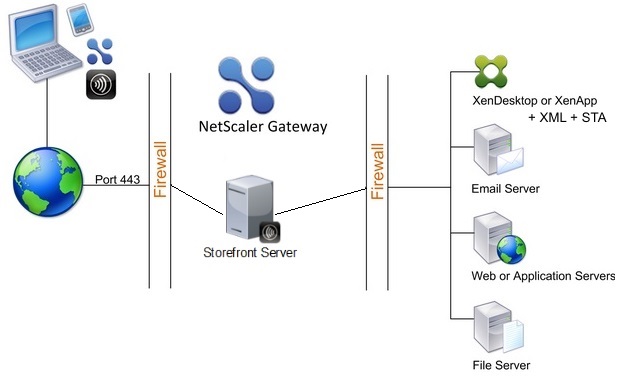
1. StoreFront in the Secure Network
In this scenario, the StoreFront resides in the secure, internal network. NetScaler Gateway is installed in the DMZ and authenticates user requests before sending the requests to the StoreFront. The StoreFront does not perform authentication, but interacts with the STA and generates an ICA file to ensure that ICA traffic is routed through NetScaler Gateway to the proper server. For small installations this is the default deployment scenario. The example of this design is shown in the Figure 1.
2. StoreFront in the DMZ
In this scenario decision where user will be authenticated determines where StoreFront will be located according to location of Netscaler gateway. There are two configurations possible:
2a. StoreFront behind NetScaler Gateway in the DMZ
In this configuration, as shown in figure 2, both NetScaler Gateway and StoreFront are deployed in the DMZ and authentication is configured on NetScaler Gateway. When users log on with Citrix Receiver, the appliance sends the NetScaler Gateway logon page to the user. The user enters authentication credentials on the logon page and the appliance authenticates the user. NetScaler Gateway then returns the user credentials to the StoreFront. NetScaler Gateway acts as a reverse web proxy for the StoreFront to route all HTTPS and ICA traffic through a single external port and require the use of a single SSL certificate.
2b. StoreFront parallel to the NetScaler Gateway in the DMZ
In this configuration, as shown in figure 3, both NetScaler Gateway and the StoreFront are deployed in the DMZ and authentication is disabled on NetScaler Gateway. Users connect directly to the StoreFront by using a web browser or Citrix Receiver. The connection occur as follows:
- User connections are first sent to the StoreFront for authentication. After authentication, the connections are routed through NetScaler Gateway.
- After users log on successfully to the StoreFront, they can access published applications or desktops in the server farm.
- When users start an application or desktop, the StoreFront sends an ICA file containing instructions for routing ICA traffic through NetScaler Gateway as if it were a server running the Secure Gateway.
- The ICA file delivered by the StoreFront includes a session ticket produced by the Secure Ticket Authority (STA). When Citrix Receiver connects to NetScaler Gateway, the ticket is presented. NetScaler Gateway contacts the STA to validate the session ticket. If the ticket is still valid, the user’s ICA traffic is relayed to the server in the server farm.
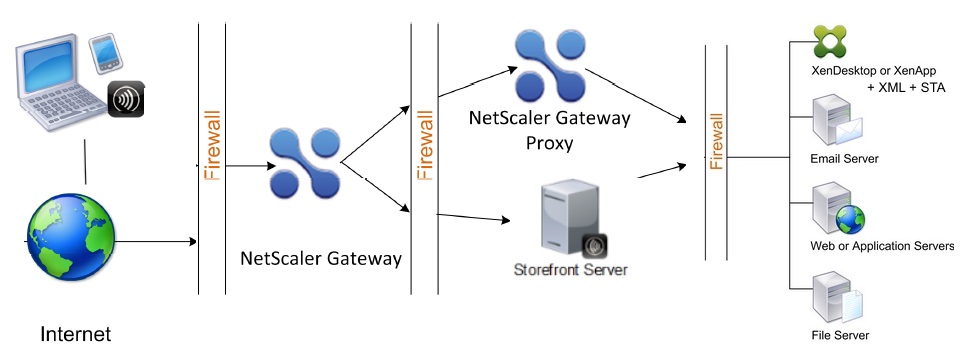
3. StoreFront in the double-hop DMZ
Double-hop DMZ is used to provide an extra security level and is based on three firewalls to divide the DMZ into two stages. You can deploy NetScaler Gateway appliances in a double-hop DMZ to control access to servers running Citrix XenApp. The connections in a double-hop deployment occur as follows:
- Users connect to NetScaler Gateway in the first DMZ by using a web browser and by using Citrix Receiver to select a published application.
- Citrix Receiver starts on the user device.
- The user connects to NetScaler Gateway to access the published application running in the server farm in the secure network.
- NetScaler Gateway in the first DMZ handles user connections and performs the security functions of an SSL VPN. This NetScaler Gateway encrypts user connections, determines how the users are authenticated, and controls access to the servers in the internal network.
- NetScaler Gateway in the second DMZ serves as a NetScaler Gateway proxy device. This NetScaler Gateway enables the ICA traffic to traverse the second DMZ to complete user connections to the server farm.
- Communications between NetScaler Gateway in the first DMZ and the Secure Ticket Authority (STA) in the secure network are also proxied through NetScaler Gateway in the second DMZ.
If you deploy NetScaler Gateway in a double-hop DMZ with StoreFront, email-based auto-discovery for Receiver does not work.
Worx Home and the NetScaler Gateway Plug-in are not supported in a double-hop DMZ deployment. Only Citrix Receiver is used for user connections.
If you deploy NetScaler Gateway in a second DMZ in two-hop setup you can only use ICA Proxy functionality. End Point Analysis are not available.
The standard double-hop DMZ configuration with Citrix StoreFront installed parallel to the NetScaler Gateway proxy is shown in Figure 4 . Users connect by using Citrix Receiver.
In the next post I will describe how the communication flow works in double-hop DMZ. Stay tuned for update.



In the past, we had always had all connections flow through our Citrix Secure Gateways (CSG) and Web Interface, both internal and external. Now we are implementing Netscaler Gateways 10.5 with Storefront 2.6 and my question is.. is it possible to have internal users connect directly to XenApp and XenDesktop service over 1494, and external users come in thru the NS over 443? Is this possible? or recommended even? I ask in part due to limitations on WAN optimization via Riverbeds not being effective with SSL traffic and we’d like to take advantage of ICA optimizations.
Thanks
Yes, Netscaler is recommended and only one available method to enable access to published resources from external network. You can create separate bacons for external and internal users or create one store and configure access for external users – see step 10 in my post XenDesktop 7 Deep Dive Part 6 – Install and configure StoreFront
In your StoreFront behind NetScaler Gateway in the DMZ.
whats is the configuration?
i.e.:-
a. How will storefront connect to the internal delivery controllers ( 443 on MUST it be connected to the internal domain?)
b.What ports must be enabled
443 from external connections
443 from DMZ storefront server to DNS, AD, CA server,
443 from DMZ storefront servers to the delivery controllers?
Thank you
Hi,
We need to configure Netscaler Gateway in 2 arm mode, which are the port required for this Configuration. Also, let us know how we need to do this by having 2 Netscaler VPX which are in place.
Regards
Ramesh
Hi,
End point analysis and Gateway plugin are supported in double-hop scenario.